Active Directory Enumeration is the process of gathering information about an AD infrastructure. Enumeration techniques aim to extract valuable data, such as user accounts, group memberships, system configurations, and other relevant network information. Enumeration plays a crucial role in security assessments, penetration testing, and understanding the structure of a network.
Domain administrators utilize the PowerShell Active Directory module, which is a collection of command-lets (cmdlet), to query and manage Active Directory objects. It is a component of Remote Server Administration Tools (RSAT) tools and modules. It can be installed via Powershell by entering the following command.
Get-WindowsCapability -Name RSAT.ActiveDirectory* -Online | Add-WindowsCapability -OnlineThe package has to be installed with Administrator rights, however, which is a major drawback. The key to running AD enumeration commands on a system without RSAT installed is the DLL located in the following directory.
C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management\v4.0_10.0.0.0__31bf3856ad364e35\Microsoft.ActiveDirectory.Management.dll
By copying the Microsoft Active Directory Management DLL to the Windows machine we wish to enumerate, we may get around this problem by obtaining it from any machine that has the RSAT installed. Import the DLL as a module by entering the following command.
Import-Module .\Microsoft.ActiveDirectory.Management.dll
User Enumeration
The Get-ADUser cmdlet, when combined with appropriate filters, will list all the users in the current domain with information about each
user. Not all returned users are active users. To identify active users we can look for accounts whose enabled property is set to 'True' as shown below.
The Logoncount Property can also be used to identify Active users. Always look out for users who have a reasonable logon count. Users with very high or very low logon count may be decoy users deliberately set up in environments with defense deception technologies.
We can get detailed information about a user account by including the Identity and Properties parameters.
To determine when the password was last set for each user in the domain, enter the following command.
To get a specific "string" on a user's attribute, enter a command such as shown below.
To identify all disabled user accounts in the Active Directory, enter the following command.
To obtain all accounts with passwords set to 'Never expire', enter the following command.
To obtain all locked user accounts, enter the following command.
To obtain all users from a specific Organizational Unit (OU), enter the following command.
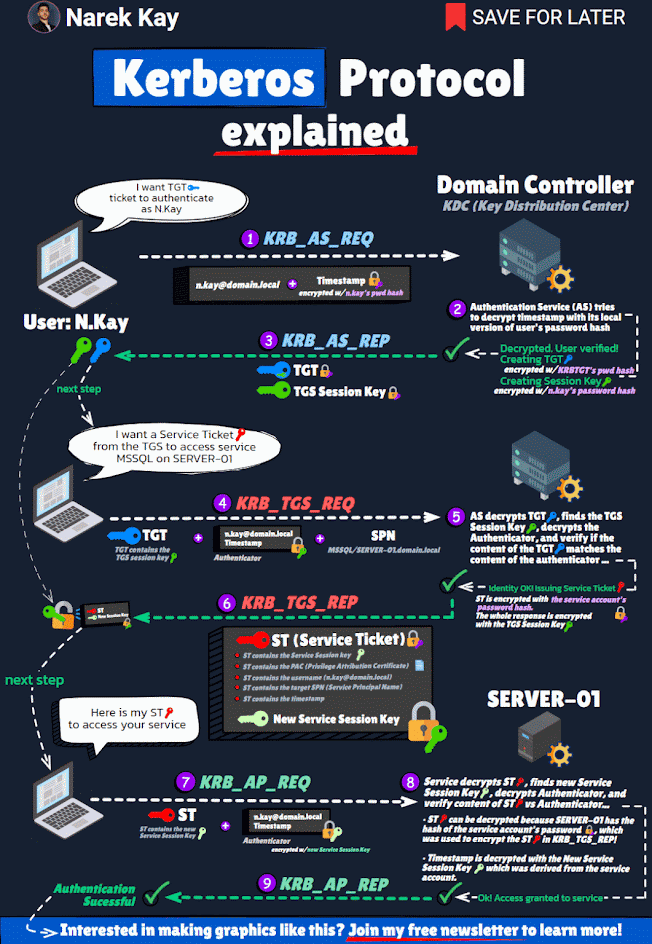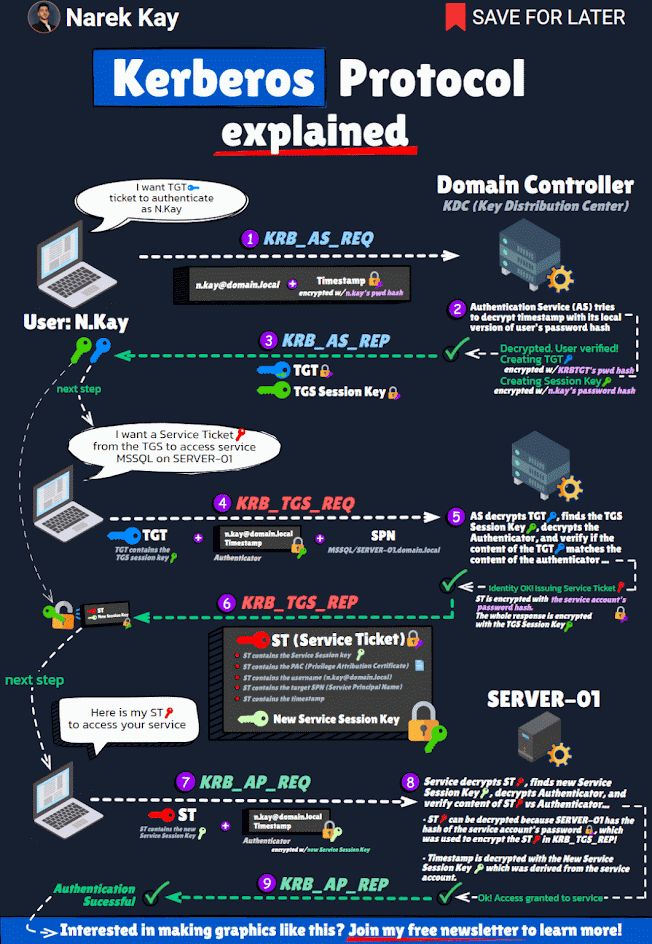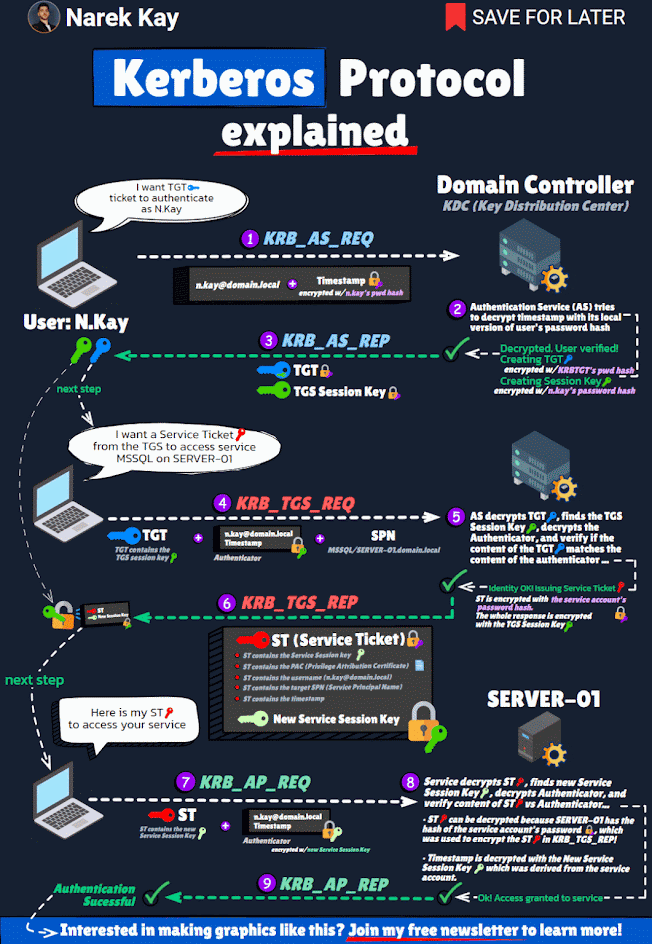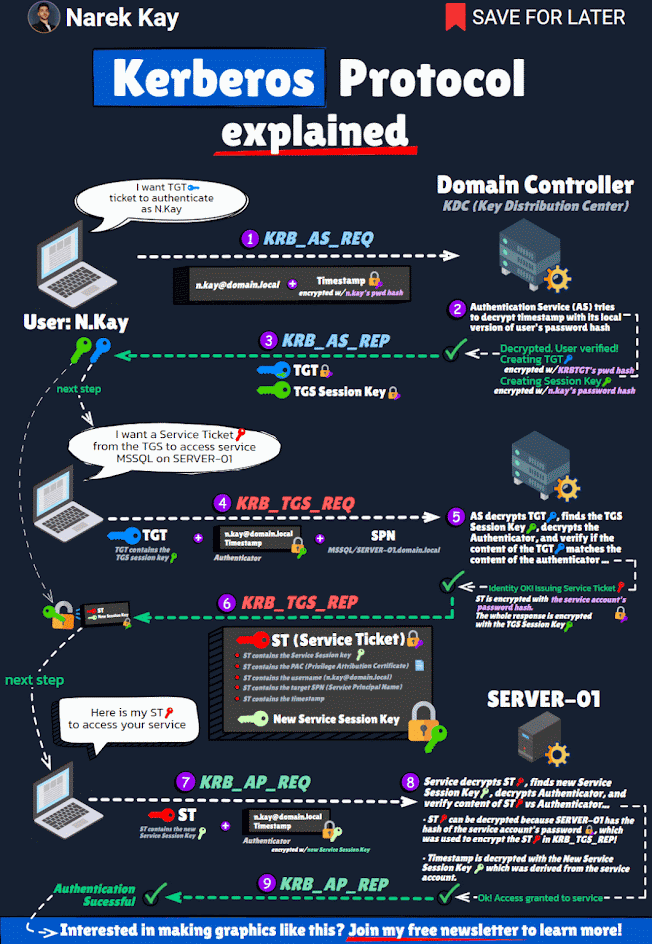
Each Active Directory domain has an associated KRBTGT account that is used to encrypt and sign all Kerberos tickets for the domain. The SID for the KRBTGT account is S-1-5-<domain>-502 and lives in the Users OU in the domain by default. 99.99% of the time, the KRBTGT account’s password has not changed since the Active Directory domain was created. The KRBTGT accounts store the Key Version Number (KVNO) in the msDS-KeyVersionNumber attribute on the KRBTGT account. Theoretically, this tracks the KRBTGT password version and is necessary for the DCs to identify which KRBTGT account was used to encrypt/sign Kerberos tickets. While the account is disabled and technically can’t be enabled, it is often one of the first accounts an attacker goes after once a Domain Controller has been compromised. The Kerberos working process tells us why.
- User logs on with Active Directory user name and password to a domain-joined computer (usually a workstation).
- The user requests authentication by sending a timestamp (Pre-auth data) encrypted with the user's password-based encryption key (password hash).
- User account requests a Kerberos service ticket (TGT) with PREAUTH data (Kerberos AS-REQ).
- The Kerberos server (KDC) receives the authentication request, validates the data, and replies with a TGT (Kerberos AS-REP).
The most important point of this process is that the Kerberos TGT is encrypted and signed by the KRBTGT account. This means that anyone can create a valid Kerberos TGT if they have the KRBTGT password hash. Furthermore, despite the Active Directory domain policy for Kerberos ticket lifetime, the KDC trusts the TGT, so the custom ticket can include a custom ticket lifetime (even one that exceeds the domain Kerberos policy). The attacker may use the KRBTGT account to persist on the network even if every other account has its password changed. At the Black Hat 2014 security conference in Las Vegas, Skip Duckwall and Benjamin Delpy spoke about a method (using Mimikatz) to generate your own Kerberos tickets (aka the Golden Ticket).
The key to this is that you need the hash for the KRBTGT account which exists in every Active Directory domain. The KRBTGT account is the account used to generate and sign every Kerberos ticket in the domain. The “Golden Ticket” method enables an attacker to create their own TGT using the KRBTGT account password hash (often extracted from a DC using Mimikatz) with a long lifetime and with any group membership they wish – remember, the TGT is encrypted/signed by the domain’s KRBTGT account which is trusted by default by all computers in the domain.
PS C:\Users\Client01> Get-ADUser -filter {SamAccountName -like "krbtgt*"} -Prop *,msds-keyversionnumber
AccountExpirationDate :
accountExpires : 9223372036854775807
AccountLockoutTime :
AccountNotDelegated : False
adminCount : 1
AllowReversiblePasswordEncryption : False
AuthenticationPolicy : {}
AuthenticationPolicySilo : {}
BadLogonCount : 0
badPasswordTime : 0
badPwdCount : 0
CannotChangePassword : False
CanonicalName : dfirnoob.com/Users/krbtgt
Certificates : {}
City :
CN : krbtgt
codePage : 0
Company :
CompoundIdentitySupported : {False}
Country :
countryCode : 0
Created : 8/24/2023 6:55:41 AM
createTimeStamp : 8/24/2023 6:55:41 AM
Deleted :
Department :
Description : Key Distribution Center Service Account
DisplayName :
DistinguishedName : CN=krbtgt,CN=Users,DC=dfirnoob,DC=com
Division :
DoesNotRequirePreAuth : False
dSCorePropagationData : {8/24/2023 7:09:36 AM, 8/24/2023 6:55:43 AM, 1/1/1601 1:04:16 AM}
Enabled : False
Fax :
GivenName :
HomeDirectory :
HomedirRequired : False
HomeDrive :
HomePage :
HomePhone :
Initials :
instanceType : 4
isCriticalSystemObject : True
isDeleted :
KerberosEncryptionType : {None}
LastBadPasswordAttempt :
LastKnownParent :
lastLogoff : 0
lastLogon : 0
LastLogonDate :
LockedOut : False
logonCount : 0
LogonWorkstations :
Manager :
MemberOf : {CN=Denied RODC Password Replication Group,CN=Users,DC=dfirnoob,DC=com}
MNSLogonAccount : False
MobilePhone :
Modified : 8/24/2023 7:09:36 AM
modifyTimeStamp : 8/24/2023 7:09:36 AM
msds-keyversionnumber : 2
msDS-SupportedEncryptionTypes : 0
msDS-User-Account-Control-Computed : 8388608
Name : krbtgt
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory : CN=Person,CN=Schema,CN=Configuration,DC=dfirnoob,DC=com
ObjectClass : user
ObjectGUID : 7c02f1a1-a5ce-4530-ab67-5ca7298b56ad
objectSid : S-1-5-21-3093783196-1193534153-587521673-502
Office :
OfficePhone :
Organization :
OtherName :
PasswordExpired : True
PasswordLastSet : 8/24/2023 6:55:41 AM
PasswordNeverExpires : False
PasswordNotRequired : False
POBox :
PostalCode :
PrimaryGroup : CN=Domain Users,CN=Users,DC=dfirnoob,DC=com
primaryGroupID : 513
PrincipalsAllowedToDelegateToAccount : {}
ProfilePath :
ProtectedFromAccidentalDeletion : False
pwdLastSet : 133373301414202961
SamAccountName : krbtgt
sAMAccountType : 805306368
ScriptPath :
sDRightsEffective : 0
servicePrincipalName : {kadmin/changepw}
ServicePrincipalNames : {kadmin/changepw}
showInAdvancedViewOnly : True
SID : S-1-5-21-3093783196-1193534153-587521673-502
SIDHistory : {}
SmartcardLogonRequired : False
TrustedForDelegation : False
TrustedToAuthForDelegation : False
UseDESKeyOnly : False
userAccountControl : 514
userCertificate : {}
UserPrincipalName :
uSNChanged : 12785
uSNCreated : 12324
whenChanged : 8/24/2023 7:09:36 AM
whenCreated : 8/24/2023 6:55:41 AM
Enumerate Domain Computers
The Get-ADComputer cmdlet displays a list of every computer object in the current domain or a specified one.
To filter active computers, check LastlogonDate, Lastlogon, and IP address properties:
The Lastlogon time is displayed in Filetime format in the above result, to display it in human-readable format, the command should be re-entered as follows:
To get a count of all computers in the domain, enter the following command.
The following command will provide a count of all computers and group them by the operating system. A great command to give you a quick inventory of computers in the Active Directory.
To obtain a list of all Windows 10 computers in the Active Directory, enter the following command. To obtain a list of any OS of interest, simply replace Windows 10 with the OS name in the command.
Enumerate Domain Controllers
The Get-ADDomainController cmdlet can get information about all domain controllers or specific ones with various search parameters. The following command will list the domain controllers by name only with no additional information.
To list available domain controllers in the current domain, enter the following command. This will not list all domain controllers but will use the DCLocator mechanism to return a discoverable DC.
The DC Locator process is used by Windows systems to locate the closest available Domain Controller within an AD Domain. It relies on DNS resolution and AD sites and subnet configuration for the identification. Read more here. You can use the -server argument followed by the fully qualified domain name to list domain controllers from another domain.
Get-ADDomainController -server Johannesburg.dfirnoob.com | Select Name, Domain, Forest, IPv4Address, Site
The properties to look out for in a domain controller include Operating system version, Operating System Hotfix, and Service Pack information. These properties help define the privilege escalation vectors.
To obtain verbose information about the domain controllers in the Active Directory, the following command can be entered.
In this article, we discussed how to import the PowerShell ActiveDirectory module and utilize it to collect pertinent information that enables us to find security holes and misconfigurations that we might exploit for privilege escalation attacks or other future actions.






















Post a Comment