Mobile devices use radio waves to communicate over the network with various frequencies and standard communication protocols. Two of the most common mobile communication protocols are Global System for Mobile Communication (GSM) and Code Division Multiple Access (CDMA). Other common mobile communication protocols include Time Division Multiple Access (TDMA) and Integrated Digital Enhanced Network (iDEN).
GSM devices uses SIM card to authenticate with the network and store various information including some user-generated activities. The SIM card's operation is analytically described in the series of ISO/IEC 7816 standards.
The first SIM card was developed in 1991 by the Munich smart-card maker Giesecke & Devrient who sold the first 300 SIM cards to the Finnish wireless network operator Radiolinja.
SIM refers to an Enhanced Data rates for GSM Evolution (EDGE) or 2G application which was introduced during the initial or early days of GSM standards, later with the introduction of 3G applications, more complex functions also got coupled with the card and SIM got evolved into USIM.
Universal Subscriber Identity Module (USIM) card is also a type of SIM card but specifically for WCDMA/UMTS (3G) phones. The USIM application, is what identifies you and your phone plan to your wireless service provider using one of these standards: Universal Mobile Telecommunications System (UMTS), High Speed Packet Access (HSPA) or Long Term Evolution (LTE).
The Universal Integrated Circuit Card (UICC) is the latest generation of the SIM card and is now being used in most smart devices including CDMA devices. UICC is the hardware portion of the smart card while 2G SIM/USIM/CSIM/ISIM are the software applications on the smart card. All the applications on the UICC are defined by ETSI and adopted by the Third Generation Partnership Project (3GPP).
A big advantage of UICC over (U)SIM, however, is that it is compatible with all mobile technologies (GSM and CDMA). UICC covers the gamut of subscriber cards to include SIM, USIM the Removable User Identity Module (R-UIM) and CDMA2000 Subscriber Identity Module (CSIM) cards, also part of the CDMA devices that can be used globally.
The physical size of a UICC is described in ETSI TS 102 221; version 11.0.0 references both ISO/IEC 7816-1 and ISO/IEC 7816-2 for acceptance. The most significant change to the UICC has been the size of the smart card. The sizes are defined by ETSI as:
- First Form Factor (1FF ID-1 UICC) - The original SIM card was the size of a credit card. The ID-1 UICC was never used in a mobile device because of its large size.
- Second Form Factor (2FF Mini-UICC) - The most commonly referenced and was found in feature phones and early smart devices until 2004.
- Third Form Factor (3FF Micro-UICC) - This is commonly referred to as the “micro-SIM.” This SIM version began appearing to field the need for 4G speeds. It is still very common today. Like previous versions, it still uses the same part of the chip but removes some of the plastic area around the mainboard.
- Fourth Form Factor (4FF Nano-UICC) - This can also be referred to as the “nano-SIM.” Like the version before it, it still utilizes the same chip area and removes even more of the surrounding plastic. It was released in 2012 and adopted in newer iOS, Android, BlackBerry, and Windows Phones.
- Embedded SIM (MFF2) - Most devices that contain SIM cards allow for user removal which allows a user to insert another SIM card that allows service to the handset. With an embedded SIM, the SIM is not removable, and this allows the user to reactivate between carriers without having to purchase a specific SIM for the network. eSIM uses the same electrical interface as a physical SIM as defined in ISO/IEC 7816. Once a carrier profile has been installed on an eSIM it operates the same as a physical SIM, complete with a unique ICCID and network authentication key generated by the carrier.

Having discussed the evolution of smart cards used in mobile communications from SIM to USIM to the latest UICC, the reader should note that from this point onwards, the term SIM card will now mean UICC. I will retain the name SIM card as this is a commonplace term, but it should be noted that UICC (and not SIM card) is meant. Also, both will be used interchangeably.
SIM Card Architecture
SIM cards contain an internal chip which has various functions. The actual SIM chip is covered by a plastic frame. However, only the connection surface, which holds communication between the device and the SIM card through a serial interface, is exposed to the user. An ISO 7816-compliant smart card (and a SIM card is one) require 5 different contact points to work: Vcc (power), ground, clock, I/O (data), and reset.
Description of SIM Card Hardware
As seen in the above figure, the UICC surface is contacted by six or eight points along reciprocal contact points on the mobile device (most UICCs in today’s devices have six pins). Reading, querying, and writing to the UICC occurs at these contact points. They are listed below.
- C1-VCC - This is the supply voltage pin. It supports the +5V DC power input.
- C2-RST - Reset signal, used to reset the card's communication.
- C3-CLK - Provides the card with a clock signal.
- C4 - AUX1, optionally used for USB interfaces and other uses.
- C5-GND - Ground, it is the common reference voltage.
- C6-VPP - Programming Voltage input, this contact may be used to supply voltage required to program.
- C7-I/O - The I/O is an asynchronous half-duplex UART-type interface, whose baud rate is determined by the card’s characteristics and the clock frequency that it is given by the reader.
- C8 - AUX2, optionally used for USB interfaces and other uses.
To operate correctly, the UICC needs all points in contact with the mobile device terminal pins.
Beneath the visible hardware components of the SIM card lies the software components which are very critical to its operation and are not visible to the user
Internally, the software components of a SIM card, include a microprocessor (CPU) and an operating system (OS). SIM card also consists of both volatile and non-volatile memory. The RAM (Random Access Memory) which is the volatile memory is used to execute programs in SIM card. The non-volatile memory types are ROM (Read Only Memory) and EEPROM (Electrically Erasable Programmable Read Only Memory).
The UICC accepts communication via the I/O contact point from the mobile device, which is the pathway to the CPU.
The ROM stores the Operating System as well as the built-in security data such as encryption scheme and user authentication. The operating system controls all access operations of SIM card files. It performs the normal operation set such as read, write, create, etc. The microprocessor and OS could be Java card that uses Java programming language platform for embedded devices or exclusive to the issuer.
The EEPROM contains the main data and the hierarchical based file system structure.
The main drawback of this design, in terms of forensics, is the lack of direct memory access. It is not possible to bypass the microprocessor since it is the one that provides the access to the memory. This makes it impossible to dump the memory contents of the SIM card, the same way as it is possible when cloning (copying bit by bit) a hard disk drive. The examiner who wants to analyze data kept in the SIM gets access using microprocessor commands, with the help of a smart card reader or by using the mobile phone itself (if the latter allows it, possibly through the use of special AT commands). In any case, forensics software can make the process easier by providing a suitable graphical user interface and automating a series of tasks.
There is no super-tool and the examiner in many cases has to work with a compilation of programs and versions in order to be able to extract as much data as possible. Software should be tested extensively since there is always chance of faulty operation, either due to bugs or due to the huge volume of standards and the possible deviations that manufacturers sometimes take.
SIM Card File System
There is only one Master file in the UICC. MF (Master File ) is the root directory with a file ID of 0x3F00. The Dedicated Files (DF) are the sub-directories of MF which are used by SIM card services. Their contents and functions had been defined by the GSM 11.11 Specifications. All DF directories identifiers starts with 0x7FXX address. Elementary Files (EF) are the actual files which contain user data thus recovering those files are the main goal of a forensics investigator. In fact, the EF file can exist under MF (memory address = 0x2FXX) or DF (memory address = 0x6FXX).
It is critical that the examiner obtain a full file system collection from the SIM/UICC and always recommended that the UICC card be collected and examined outside the body of the device, no matter the device, for reasons that include but are not limited to network location, networks accessed, subscriber information, SMS, contacts, and calls, to name a few. Each of these records can also contain information that an automated tool either cannot parse or does not parse correctly, so manual inspection is sometimes necessary.
All SIM cards consist of two parts of data storage. One part is used for system or network information and the other is used for user information which is locked by user PIN code.
Network Information
They contain information used by the mobile device to communicate on the network in a format that makes sense only to the network of the carrier system engineer.
The fact that the user usually cannot directly access them, and as such it is more difficult for him to delete them, is of great importance in a forensic investigation. A criminal, not knowing these details, will not be able to erase incriminating data leaving behind valuable evidence. Moreover, it is possible to verify these data in comparison to the ones the provider retains and spot a possible forgery.
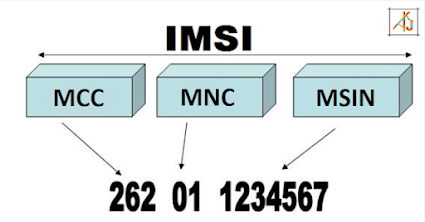
International Mobile Subscriber Identity (IMSI) = EF_IMSI
The International Mobile Subscriber Identity (IMSI) is the unique number that identifies the subscriber on the cellular network. This number is used to find a subscriber across the network and deliver calls, data, and other transactional information. Often, examiners think the phone number of the device is important to a cellular network. But it is the IMSI, for both GSM and CDMA networks, that is needed for contact to be made.
IMSI number allows the SIM to be identified, even if the card itself has expired and its use is not possible in the network. This information is present in EF_IMSI (file ID 0x6F07 = 28423).
The IMSI is a protected file, and as such, if the UICC is locked with a PIN it will be inaccessible. The IMSI, under GSM/UMTS standards, will be 9 bytes, but the subscriber number can be a maximum of 15 digits.
The IMSI structure is as follows:
IMSI = MCC+MNC+MSIN
Where
- MCC (Mobile Country Code) is the three digits country code
- MNC (Mobile Network Code) is the two digits mobile telephony network code (three digits in USA and Canada).
- MSIN (Mobile Subscriber Identity Number) - This is the user’s mobile telephony serial number and consists of 10
digits (9 digits in USA and Canada).
For example, 310 410 123456789 is 15 digits IMSI where 310 refers to country code “US”; 410 refers to network code “AT&T”; 123456789 refers to the unique subscriber ID number. You can look up an MCC and MNC here.
The IMSI number is critically important number and can be used to eavesdrop telephone conversations and intercept mobile phone traffic and track the location of a user by a powerful adversary with sufficient resources such as a Nation-state. An IMSI-catcher will be the tool used here. It is essentially a fake mobile tower acting between the target mobile phone and the real towers of the service provider. It is considered a Man-In-The-Middle attack. The 3G wireless standard offers some risk mitigation due to mutual authentication required from both the handset and the network. However, sophisticated attacks may be able to downgrade 3G and LTE to non-LTE network services which do not require mutual authentication.
Integrated Circuit Card Identifier (ICCID) = EF_ICCID
The ICCID is analogous to the serial number of the UICC; it represents the unique number assigned to that single UICC. In other words, no other smart card on the cellular network uses the same unique number. It is a unique serial number which corresponds to the printed card circuit and is based on ITU-T E.118. This information is present in the SIM file (EF_ICCID, file ID 0x2FE2 = 12258).
The ICCID is made up of 10 bytes that comprise several values. ICCID data is stored in reverse nibble format in 19 - 20-digit number including a single check digit as a checksum.
MMCCIINNNNNNNNNNNNCx- MM = Constant (ISO 7812 Major Industry Identifier)
- CC = Country Code (1-3 digits)
- II = Issuer Identifier
- N{12} = Account ID ("SIM number")
- C = Checksum calculated from the other 19 digits using the Luhn algorithm.
- x = An extra 20th digit is returned by the 'AT!ICCID?' command, but it is not officially part of the ICCID.
Country calling codes according to ITU-T E164 are the known codes we use in the phone network when we call foreign countries. For example, UK possesses number 44, Germany possesses number 49, France 33, Italy 39, and so on.
The extracted value is “98 07 91 09 02 24 02 71 33 F0” and can be read as “89 70 19 90 20 42 20 17 33 0”. The first byte “89” refers to industry identifier of telecommunications. “7” refers to the country code “Russia”; “01” refers to network code “MTS”. The remaining values “99020422017330” refer to some account information such as account ID and checksum. We can check the extracted ICCID number using the SIM number analysis tool provided by the International numbering plans.
The ICCID must always be available to the mobile device without limitation, primarily because this number will be used for the authentication process. This means that even if a UICC is locked with a PIN, the ICCID can be ascertained, and the examiner can then use the ICCID to obtain the PIN unblocking key (PUK) to change the PIN and access the UICC contents by sending the carrier of record the appropriate court order.
Local Information (LOCI)
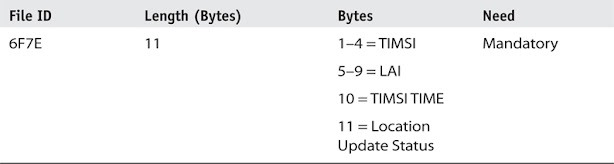
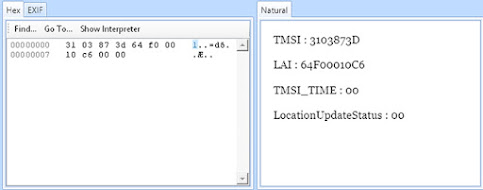
The Location Information (LOCI) is an Elementary File (EF_LOCI, file ID 0x6F7E = 28542) under the DF_GSM (DF structure for GSM) that identifies the geographic area where the device was last successfully powered off.
The LOCI writes the last tower location to which the device was registered when a successful power off occurred so that the device can access the network quickly upon powering on. If the device’s battery is removed, is not powered off correctly, or it is broken prior to powering off, this file may not be available or may be incorrect. If, in fact, the LOCI file contains data, the examiner can use this key to identify the geographic location by contacting the carrier of record with the key information. The LOCI comprises the TMSI (Temporary Mobile Subscriber Identity), LAI (Location Area Information), TMSI Time, and the location update status.
The TMSI, as indicated by its name, is a temporary random ID that is assigned via the VLR (Visitor Locator Register) to the subscriber; the actual IMSI is not sent out via the handset because of possible capture and identification of the mobile subscriber, and the temporary IMSI changes when the device moves to a different VLR.
The Visitor Locator Register (VLR) is a database of information about a roaming subscriber.
The TMSI is four octets long and will make no sense to the investigator. However, the investigator could contact the carrier for assistance with determining the location represented by the TMSI.
The LAI comprises the MCC (Mobile Country Code), the MNC (Mobile Network Code), and the LAC (Location Area Code). By consulting this site, the examiner can at least identify the country and carrier to contact and obtain possible subscriber information.
The figure below shows the identifiable information for the LOCI.
Mobile Subscriber Integrated Services Digital Network Number (MSISDN) = EF_MSISDN
In general, MSISDN consists of the Country Code (CC – up to three-digits), the National Destination Code (NDC – up to 3 digits), and the Subscriber Number (SN – up to 10 digits), with a maximum of 15 digits total.
MSIDSN is an optional elementary file (i.e., Optional EF does not need
to be stored on the SIM card itself), which differentiates it from both
ICCID and IMSI (which are mandatory fields). Own Dialing Number is a
similar service that allows mobile users to inquire about their telephone numbers by dialing a specific numeric code.
Forbidden Public Land Mobile Network (FPLMN)
Forbidden Public Land Mobile Network (FPLMN) is an Elementary File under DF_GSM that identifies networks with which the device carrier does not have a valid agreement to access. In other words, a PLMN (both MCC and MNC) will be written to the FPLMN if the network rejects the location update, because PLMN is not allowed.
It can hold up to any number of records, depending upon the card manufacturer and carrier specifications. When a record is added to the FPLMN Elementary File, that record is placed after the last record; if there are no additional slots, the first record is removed and the new record is added to the last available slot.
In terms of value for the examiner, the FPLMN identifies specific country codes along with the carrier of record, which could also identify a geographic region in which the mobile device was being used or attempted to access. If a user, for example, had stated that he was not in a certain country and admitted to having control of the mobile device, but access was attempted to a forbidden network in the country the user denied being in, an argument could be made that the user was indeed within the country.
User Data Information
When examining the information from a mobile device UICC, forensic investigators primarily focus on personal data that could be stored on the SIM. With the storage capacity of today’s mobile devices, the storage of personal data to the UICC is not the norm. Mobile device settings default to storage to the handset, and a user would have to change the storage location settings manually for the UICC to be used. Because the capacity of a SIM is finite, the storage of data that can be used for investigations is limited. This does not dismiss the importance of collecting the UICC content, however.
From the user part, contacts, call logs, and SMS could be recovered as discussed below.
Short Message Service (SMS)
The Short Message Service (SMS) is another Elementary File located on the UICC (EF_SMS, file ID 0x6F3C = 28476). The SMS body is encoded using a special 7-bit encoding called GSM 03.38 encoding or Unicode for non-English characters.
Either 3GPP TS 23.040 or ETSI 123 040 for UMTS defines these records as messages that either originate from the mobile equipment (ME) or are received from the subscriber’s network. The record length cannot be more than 176 bytes, with the first byte being a status of the record and the remaining bytes making up the architecture of the message. The values for the status bytes is shown in the figure below.
The status byte of the record, shown above will tell the examiner several interesting facts. If the status byte indicates “Unused” and content is still contained within bytes 2–176, the examiner should assume, with great certainty, that the message has been deleted. When the user deletes a text message, instead of the message being fully erased, the only change taking place is that this first byte gets the value 0, marking the slot free for use. The remaining contents at the location that the message existed remain intact. The figure below shows the hex dump of an SMS.
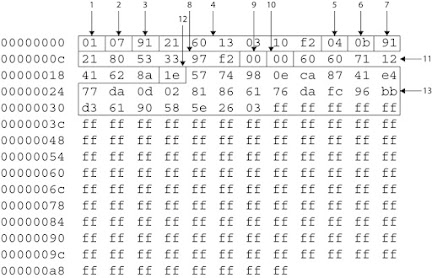
- The first byte has the value “01” which indicates that this SMS was read.
- The second byte indicates the number of bytes used for the short message service center (SMSC) number. In this case, it has the value of 7, which means the next 7 bytes “91 21 60 13 03 10 F2” determine the service center number.
- This byte is used to identify the type of SMSC number, The value "91" in this case means the international format.
- The rest of 6 bytes “21 60 13 03 10 F2” give the SMS center number in reverse nibble format. Thus, the SMSC number is “1 206-313 0012”.
- First octet of SMS-DELIVER message (04 = SMS-DELIVER).
- Length of sender address (0B = 11)
- This byte identifies the type of sender SMSC number (0x81 - unknown or 0x91 - international number).
- The following bytes “21 80 53 33 97 F2” of specific length give the contact number of the sender of the message which is “1 208-353 3792”.
- Protocol identifier ( The value here is 0x00).
- This byte is used to indicate the encoding type of message body (0x00 means the default 7-bit encoding is used).
- This is the 6-bytes timestamp data “60 60 71 12 41 62” which contains the date and the time when the SMS was sent. The date (Year, Month, Day) and time (Hour, Minute, Second) are stored in reverse nibble format. Thus, “60” means “2006” year, “60” means “June” month, and “71” means “17th” day. Also for the time, “12 41 62” is decoded to “21:14:26” in the format (hh: mm:ss). Finally, we can observe that the message was sent in (June 17, 2006 21:14:26 PM).
- This byte indicates the length of user data (1E = 30).
- The last record is used for the message content (7-bit encoding). In our example, the SMS content data is “57 74 98 0E CA 87 41 E4 77 DA 0D 02 81 86 61 76 DA F6 9C BB D3 61 90 58 5E 26 03”. This data can be decoded using any simple 7-bit encoder. We use the encoder provided at the link. The message content is "What ya doin Cali6Osnia bred" as shown below:
SMS forensics is a wide topic whose discussion will have to be left to a later post.
Abbreviated Dialling Numbers (Contact List)
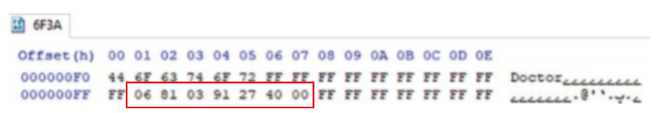
Contacts on a UICC are referred to as Abbreviated Dialing Numbers (ADN). This Elementary File (EF_ADN , file identifier 0x6F3A = 28474), is located on a SIM application under DF_Telecom and can also be under DF_Phonebook on a USIM application. Often these phonebooks coexist and contain duplicate records, but it is entirely possible that the records under DF_Phonebook on the USIM are unique and accessible only by reading the DF_Phonebook on the USIM application. The phonebook located on the USIM application is under the DF_Phonebook, which is under DF_Telecom. This is referred to as the global phonebook.
Multiple phonebooks are available under the DF_Telecom/DF_Phonebook and can be application specific. This means that a single phonebook under DF_Phonebook can be used by a single application on the mobile device up to 250 record entries. UICCs with the DF_Phonebook can hold thousands of contact names and numbers, and this Dedicated file should be investigated.
Due to limited memory resource, some of SIM cards may use EXT1 (0x6F4A) EF records to save additional data of ADN. In memory, the contact's name is stored in ASCII code format as a plain text. The contact number associated with the contact name comes on the next record. The contact number record has a special format where each group of bytes refers to a certain information. The first byte indicates the number of bytes used for the number in the record. The next byte will have either 0x81 or 0x91 hex values. If the number is an unknown number then the value will be 0x81. However, this byte gets 0x91 value when the contact number is an international number. The rest of bytes which the length of it is specified by the first byte are for the contact number itself. The format used for storing contact number is the reverse nibble which means the least significant 4-bits must be read first in a byte.
The contact name in this example is “Doctor” which can be decoded using ASCII code encoder. The next record is for the associated phone number of “Doctor”. The first byte has the value of “06” which indicates that the number of bytes used for the contact number is 6 bytes. The next byte has the value of 0x81 which means this phone number is either local or unknown. The rest used bytes are “03 91 27 40 00”. To decode the number, we should remember that the number is stored in reverse nibble order thus the decoded number is “301-972 0400”.
Call Logs
A UICC stores only the last numbers dialed (LND) in the Elementary File (EF_LND file ID 0x6F44 = 28484) and does not store incoming calls to the SIM memory. Incoming calls would be stored on the device itself. The Elementary File (EF_LND) is located under DF_Telecom in both the SIM and USIM application. The EF_LND record is similar to the EF_ADN in the storage capacity and data layout.
SIM Security
Based on the application, the access operations over files are controlled by permissions that associated with the files. All MF, DF, and EF files are associated with security permissions at various levels. The Personal Identification Number (PIN) is used to protect the data of the subscriber where this code (4–8 digits) is used for verification.
At the secondary level, the PIN2 code also exists for the management of certain phone characteristics (e.g. network settings, restriction of possible calls only to specific numbers, and so on).
At this point, we must note that the right term as it is reported in standards is CHV (Card Holder Verification) and not the term PIN (Personal Identification Number) which has prevailed. The PIN is originally set by the manufacturer or the provider but it can also be changed by the subscriber. This can be done using phone’s settings or using network codes
**04*old PIN*new PIN*new PIN#
for PIN1, and
** 042*old PIN*new PIN*new PIN#
for PIN2
There are a fixed number of tries to enter the valid PIN code, usually, three attempts. Therefore, counting the remaining number of guessing tries is very important because failure to provide the valid PIN code in three attempts will block the SIM card. This happens in order to protect the card from brute force attacks where someone would try (with the help of software), all the 10,000 possible combinations (0000-9999) for a 4 digit PIN. Fortunately, it is possible to unlock the card with the use of PUK (PIN Unblocking Key or, more formally Unblock CHV). As a matter of fact, to unblock PIN1 we use PUK1 and for unblocking PIN2 we use PUK2. PUKs consist of 8 digits and are once again set from the manufacturer or the provider. They can be changed too with network code.
**05*old PUK*new PUK*new PUK#for PUK1 and
**052*old PUK*new PUK*new PUK#for PUK2.
Caution must also be taken here as after 10 unsuccessful PUK password tries, the card is rendered useless, and the user has to visit the provider to issue a new SIM card.
As an investigator, firstly, the SIM card must be removed from the device especially if the PIN code is locking the device. Therefore, the SIM and the device are handled alone. Most of commercial tools such as Cellebrite and XRY show a warning message when the SIM locking code is enabled.





.png)
.jpeg)
.jpeg)
.jpeg)


Post a Comment