Computer systems organize memory into fixed-size pages just as they organize file systems into fixed-size disk blocks. This size is generally 4 KB or 4 MB depending on the hardware architecture. The usage of this memory is centrally controlled by the memory manager. The memory manager provides a set of core services e.g. allocating memory to pages, sending data to page files when needed and bringing them back, and sharing the limited memory among files. Since the amount of available memory is small therefore most operating systems including Windows use a concept called virtual memory. According to this concept, any process running on 32-bit Windows systems is allocated a set of virtual memory addressees of 4 KB in size. Half of this size is reserved for the private use of the process and the remaining half is for the operating system use.
Virtual to Physical Address Translation
The memory manager maintains page tables for every process that needs to keep their addresses and the CPU will translate these virtual addresses into physical addresses. For each virtual address is given its own space called page table entry (PTE). In this PTE the virtual and physical addresses are mapped with each other. Windows uses a two-level page table structure to translate virtual to physical addresses. In this case, the virtual address of a process is divided into three parts; page directory index, page table index, and byte index (page frames). The purpose of each of these structures is as follows:
- The page directory index is used to locate the page table in which the virtual address's PTE is located.
- The page table index is used to locate the PTE, which, as mentioned earlier, contains the physical address to which a virtual page maps.
- The byte index finds the proper address within that physical page.
The figure below shows the relationship between these three values and how they are used to map a virtual address into a physical address.
 |
| Virtual to physical address translation process (x86 specific) |
The following basic steps are involved in translating a virtual address:
- The Memory Management Unit locates the page directory for the current process by setting a special register called the CR3 register with the address of the page directory table.
- The page directory index is used to locate a specific page directory entry (PDE) which describes the position of the page table needed to map the virtual address. The physical address within the PDE is referred to as the page frame number (PFN).
- The page table index is used to locate a particular page table entry (PTE) that describes the physical location of the virtual address being translated.
- The PTE is necessary to locate the physical memory page. If the page is valid (valid bit set to one), the PTE contains the page frame number of the page in physical memory. Conversely, if the page is invalid (valid bit set to zero) the Memory Management Unit fault handler locates the page and tries to make it valid.
- When the PTE is pointed to a valid page, the byte index is used to locate the address of the desired data within the physical page.
Page File Management
Physical memory is limited in capacity compared to the big space reserved for each process by the memory management unit. Therefore, not all processes can be accommodated in the memory at the same time. To cope with this problem the memory management unit uses a technique called paging. In this technique pages of 4 KB in size are paged out to the hard disk thus freeing space for more processes in memory. Which pages should be paged out to page file entirely depends on the operating system and application developers. Different algorithms are used for this purpose like first in first out (FIFO), last in first out (LIFO), and the priority level of the data.
When a page is swapped out to a page file it is also marked in
the corresponding page table in the memory. The same procedure is used to bring the
page back to memory when referenced. There are some pages that cannot be paged to
page file these consists of ranges of system virtual addresses that are guaranteed to be
resident in physical memory at all times. The paged-out pages are stored in one or more
files with the name pagefile.sys. By default, the page file is located in C:/pagefile.sys or
in C:/windows/win386.swp in Windows 9x systems. On Windows systems up to
16 different page files may be present. In most cases, the size of the page file is 1.5 to 3 times
the size of the installed physical memory on the computer. It is not mandatory that a page
file should be utilized when the physical memory is exhausted; a small portion of space
in the page file will still be used even when there is no paging. In this case, the page file will
be allocated to virtual memory pages for which no corresponding pages are available in
physical memory.
It is important to note that pagefile.sys is a hidden system file, and cannot be directly accessed or read by users, including administrators. However, with the right tools (such as FTK Imager) and techniques, forensic investigators can extract and analyze the content of pagefile.sys to gather relevant information for their investigations. It resides by default at
%SystemDrive%\pagefile.sys; however, a user can change its default
location. To learn the exact location of pagefile.sys (or if in doubt), check the following
registry key:
HKEY LOCAL MACHINE/System/CurrentControlSet/Control/Session Manager/Memory ManagementIt is also worth noting that Windows provides a pagefile clearing option, effectively wiping out the pagefile’s contents. However, this will only occur upon system shutdown. If the power is pulled, there will be no pagefile wiping; the same is true if the system is placed into hibernation mode. Pagefile wiping works even if the pagefile is distributed across multiple partitions or disks. Although it is unlikely to be encountered by investigators, it is something of which they should be aware. Specifically, it means that post-mortem analysis of the pagefile from such a system will not be possible. Fortunately, this is not the system’s default pagefile behavior.
Pagefile.sys Forensic Analysis
When it comes to analyzing pagefile.sys, various tools, and techniques are available. I am going to use the strings command which is built in many Linux distributions and grep with regex to fetch URLs, email directories, and other artifacts. By analyzing memory artifacts, including pagefile.sys, investigators can uncover information such as user SIDs, browser sessions, and other forensic artifacts that reside in memory.
To extract all the URLs visited by the target user, enter the following command:
strings pagefile.sys | egrep "^https ?://" | less
To fetch all the paths/directories on the suspect pagefile, enter the following command:
strings pagefile.sys | egrep -i “^[a-z]:\\\\” | sort | uniq | less
To print all email addresses from the suspect pagefile, enter the following command:
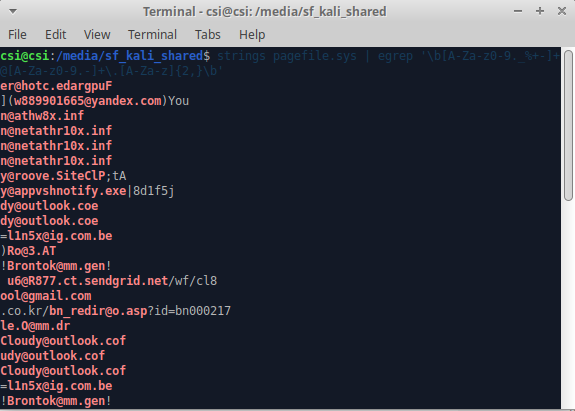
strings pagefile.sys | egrep '\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}\b'
To extract all the IP addresses from the suspect pagefile, execute the following command:
strings pagefile.sys | egrep '(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)'
To fetch all Security Identifiers (SIDs) that may be contained in the suspect pagefile, enter the command below:
strings pagefile.sys | egrep -i '/^S-1- [0-59]-\d {2}-\d {8,10}-\d {8,10}-\d {8,10}- [1-9]\d {3}/'
In conclusion, pagefile.sys is a significant component of Windows memory management, and analyzing it can provide valuable insights for forensic investigations. Tools like page_brute.py and Magnet Forensics' solutions can also aid in the analysis of pagefile.sys and extraction of crucial artifacts from memory.




It was great, thanks Joseph
ReplyDeletePost a Comment